WebRTC blackbox reverse engineering experts Gustavo and Fippo take a look at Cloudflare’s new WebRTC implementation, how Cloudflare uses the new WebRTC-based streaming standards WHIP and WHEP, and the bold pronouncement that they can be a replacement to open source solutions.
Blackbox Exploration
Meet vs. Duo – 2 faces of Google’s WebRTC
A very detailed look at the WebRTC implementations of Google Meet and Google Duo and how they compare using webrtc-internals and some reverse engineering.
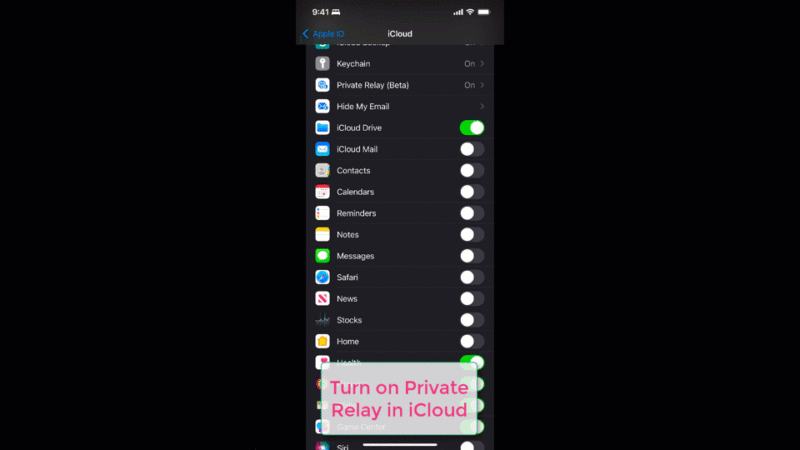
Apple’s not so private relay fails with WebRTC
Apple released iOS 15 with iCloud Private Relay broken for WebRTC – it still divulges your IP address. This post walks through why and how the WebRTC API’s use your IP address information and how you can check what IP addresses are gathered.
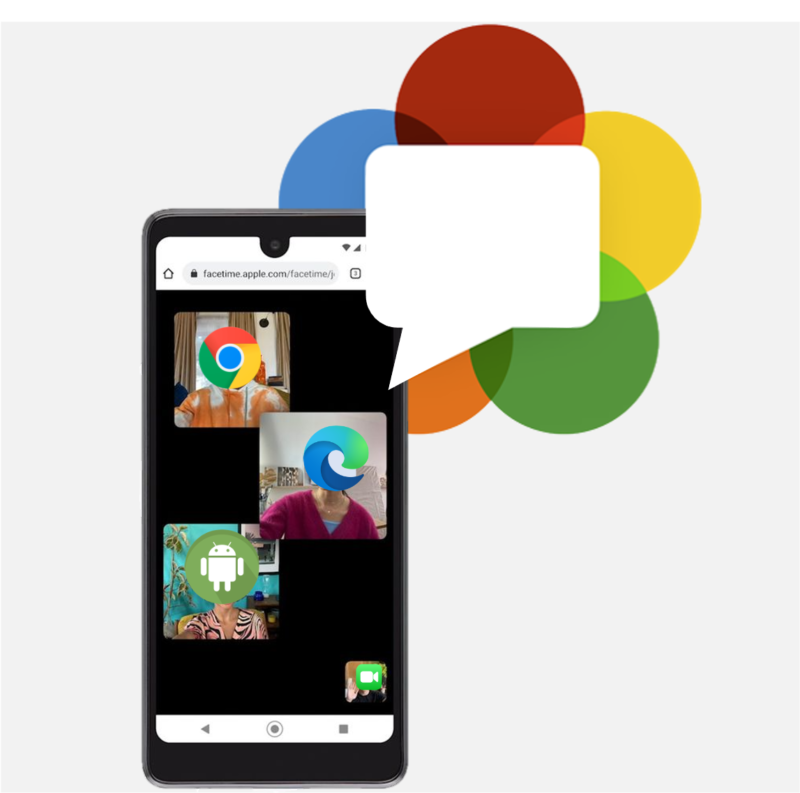
FaceTime finally faces WebRTC – implementation deep dive
Deep dive analysis on how FaceTime for Web uses WebRTC. Philipp “Fippo” Hancke uses webrtc-internals, Wireshark, and reviews the JavaScript implementation to expose Apple’s implementation details.
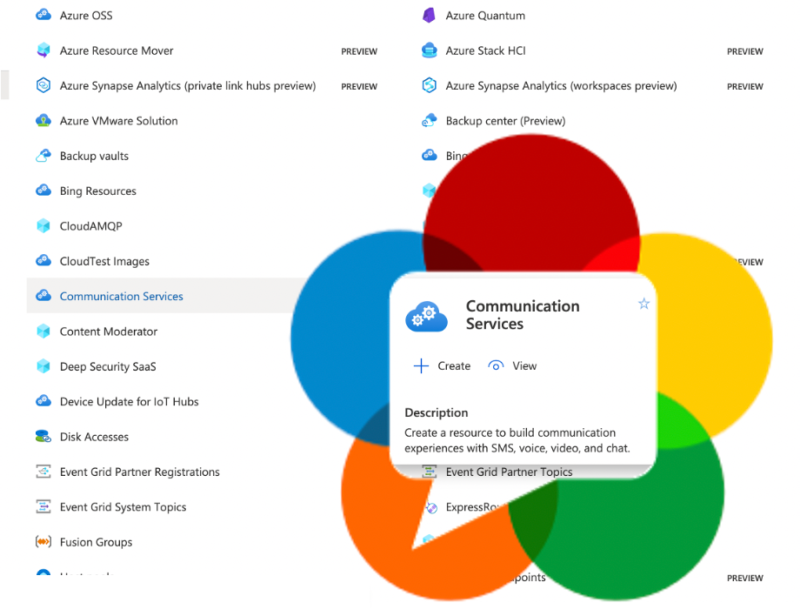
How does the new Azure Communication Services implement WebRTC? (Gustavo Garcia)
Walkthrough and deep analysis of how Azure Communications Service makes use of WebRTC by Gustavo Garcia