We covered End-to-end encryption (E2EE) before, first back in 2020 when Zoom’s claims to do E2EE were demystified (not just by us; they later got fined $85m for this), followed by the quite exciting beta implementation of E2EE in Jitsi using Chromium’s Insertable Streams API. A bit later we had Matrix explain how their approach […]
The Hidden AV1 Gift in Google Meet
Earlier last week a friend at Google reached out to me asking Does Meet do anything weird with scalabilityMode? Apparently, I am the go-to when it comes to Google Meet behaving weirdly :). Well, I do have a decade of history observing Meet’s implementation, so this makes some sense! It turned out that this was […]
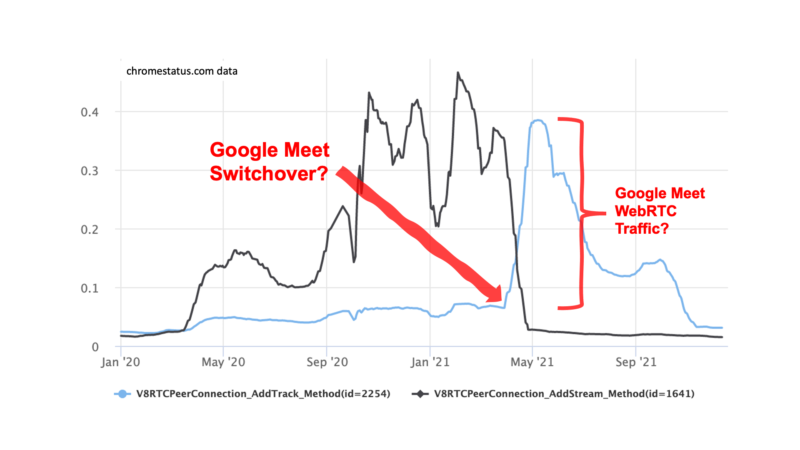
How is WebRTC doing and who is driving usage? (Hint: Google Meet)
I have been looking at these Chrome usage statistics available on chromestatus.com for a while together with Tsahi Levent-Levi for WebRTC Insights but they are too fascinating to keep them behind our paywall. Let’s do some coffee ground reading on the usage of a number of important APIs and what it tells us about what […]
Apple’s not so private relay fails with WebRTC
Apple released iOS 15 with iCloud Private Relay broken for WebRTC – it still divulges your IP address. This post walks through why and how the WebRTC API’s use your IP address information and how you can check what IP addresses are gathered.
Dealing with HTMLMediaElements and srcObjects in WebRTC applications
Philipp Hancke discusses a how to properly release Media Element resources with WebRTC and a recent Chrome issue that apps to stop handling larger numbers of participants.