webrtcHacks celebrates our 10th birthday today 🎂. To commemorate this day, I’ll cover 2 topics here: Our new merch store Some stats and trends looking back on 10 years of posts We have the Merch In the early days of webrtcHacks, co-founder Reid Stidolph ordered a bunch of stickers which proved to be extremely popular. […]
Search Results for: hancke
How Cloudflare Glares at WebRTC with WHIP and WHEP
WebRTC blackbox reverse engineering experts Gustavo and Fippo take a look at Cloudflare’s new WebRTC implementation, how Cloudflare uses the new WebRTC-based streaming standards WHIP and WHEP, and the bold pronouncement that they can be a replacement to open source solutions.
Meet vs. Duo – 2 faces of Google’s WebRTC
A very detailed look at the WebRTC implementations of Google Meet and Google Duo and how they compare using webrtc-internals and some reverse engineering.
Optimizing WebRTC Power Consumption (Markus Handell)
The performance of WebRTC in Chrome as well as other RTC applications needed to be improved a lot during the pandemic when more people with a more diverse set of machines and network connections started to rely on video conferencing. Markus Handell is a team lead at Google who cares a lot about performance of […]
How is WebRTC doing and who is driving usage? (Hint: Google Meet)
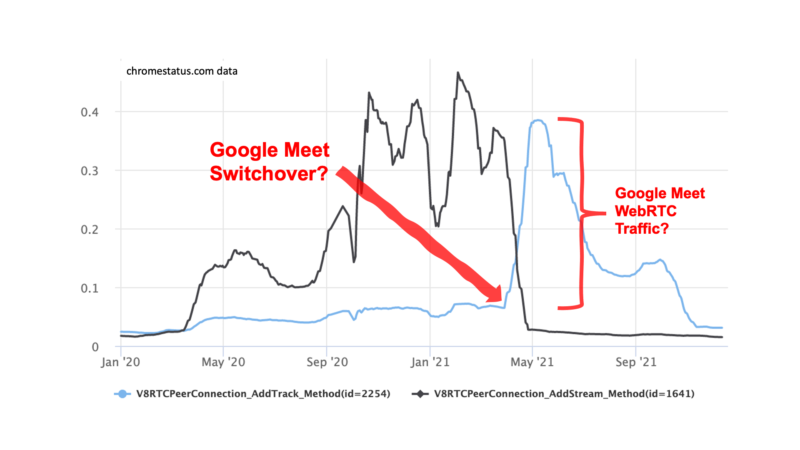
I have been looking at these Chrome usage statistics available on chromestatus.com for a while together with Tsahi Levent-Levi for WebRTC Insights but they are too fascinating to keep them behind our paywall. Let’s do some coffee ground reading on the usage of a number of important APIs and what it tells us about what […]